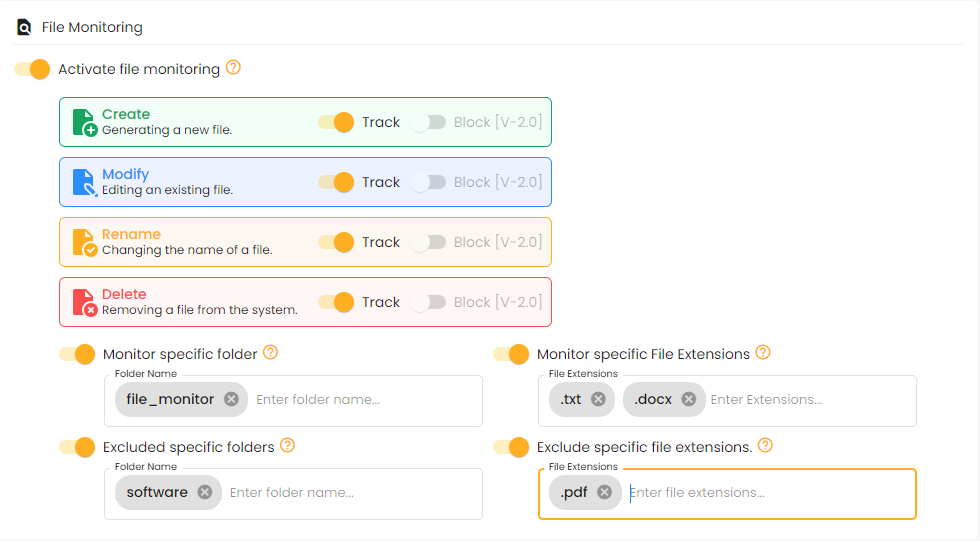
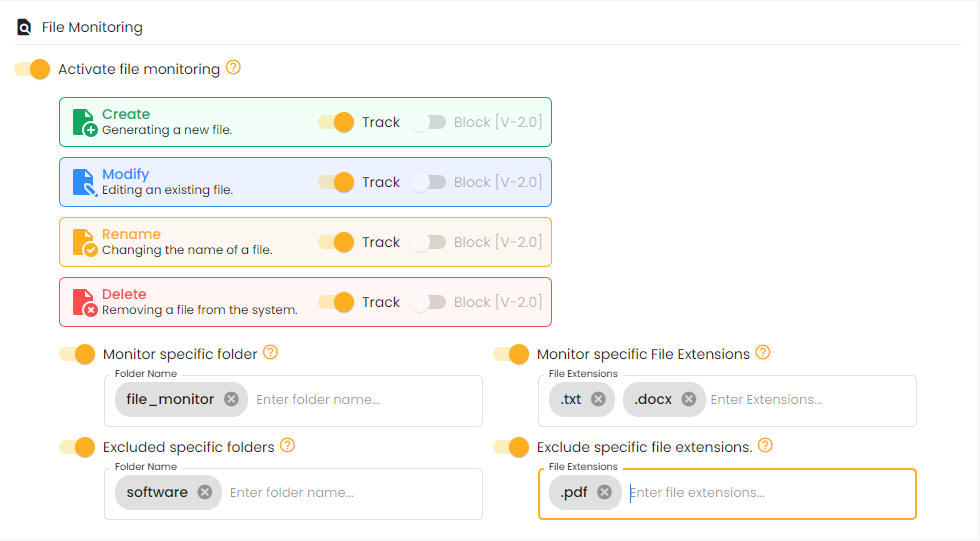
File Monitoring
To track and manage file operations like creation, modification, renaming, and deletion..
Kntrol monitors user activities on multiple systems in real-time, ensuring compliance and security by detecting and preventing threats, while simplifying administrative tasks through its user-friendly interface and collaborative features.

At Kntrol, we’re revolutionizing the way businesses safeguard their endpoints, data security and enhance productivity. Our cutting-edge endpoint monitoring and control software offers a comprehensive suite of features designed to keep your organization secure, compliant, and efficient. Let’s take a closer look at how Kntrol works and the advanced capabilities it brings to your fingertips.
Stay ahead of potential threats by capturing audio and video feeds of user activities. With this feature, you can visualize and analyze interactions in real-time.
Gain valuable insights into employee productivity and behavior with detailed activity reports. Understand how your workforce operates and identify areas for improvement.
Detects idle periods and optimizes resource allocation to maximize efficiency. Keep track of inactive users and ensure optimal workforce utilization.
Maintain a log of user logins and logouts for enhanced security and accountability. Keep a close eye on user sessions to track access and identify potential security risks.
Visualize user interactions and detect anomalies with screen capture functionality. Monitor user activity and troubleshoot issues with ease.
Safeguard your data by security control on USB device connections and activities. Prevent unauthorized access and data breaches with real-time alerts.
Keep track of printing activities and manage printer usage effectively. Monitor document printing and reduce unnecessary costs.
Prevent data leaks by monitoring clipboard activities. Control data transfer and protect sensitive information from unauthorized access.
Ensure compliance and security by monitoring email communications. Detects potential threats and policy violations in real-time.
Monitor application usage to ensure compliance and security. Track software usage patterns and enforce licensing agreements.

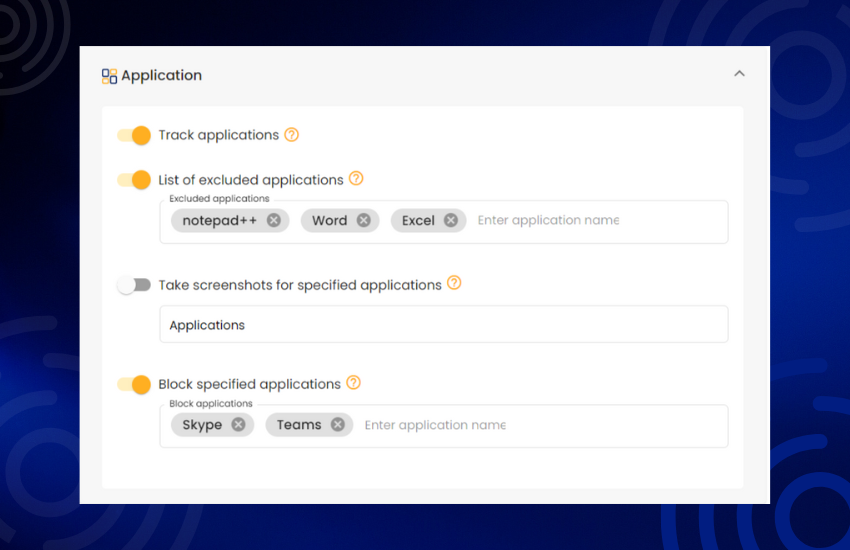
Manage application usage and enforce security policies. Control access to unauthorized applications and maintain a secure environment.
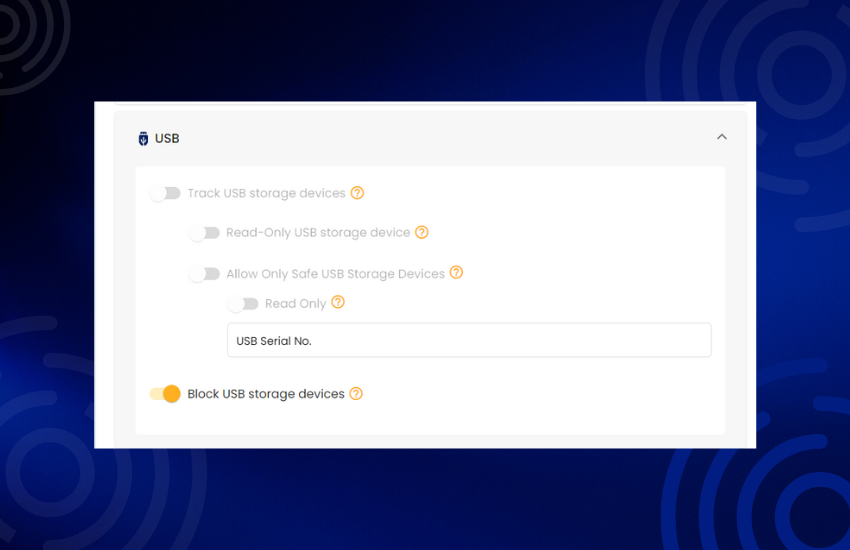
Control USB device usage and prevent data breaches. Block unauthorized devices and protect sensitive information.
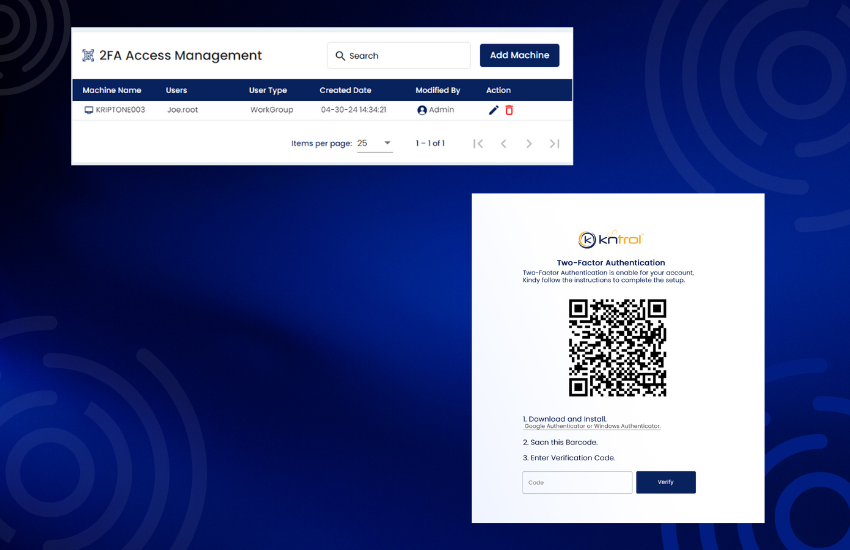
Strengthen security with two-factor authentication. Enhance access control and protect against unauthorized access attempts.
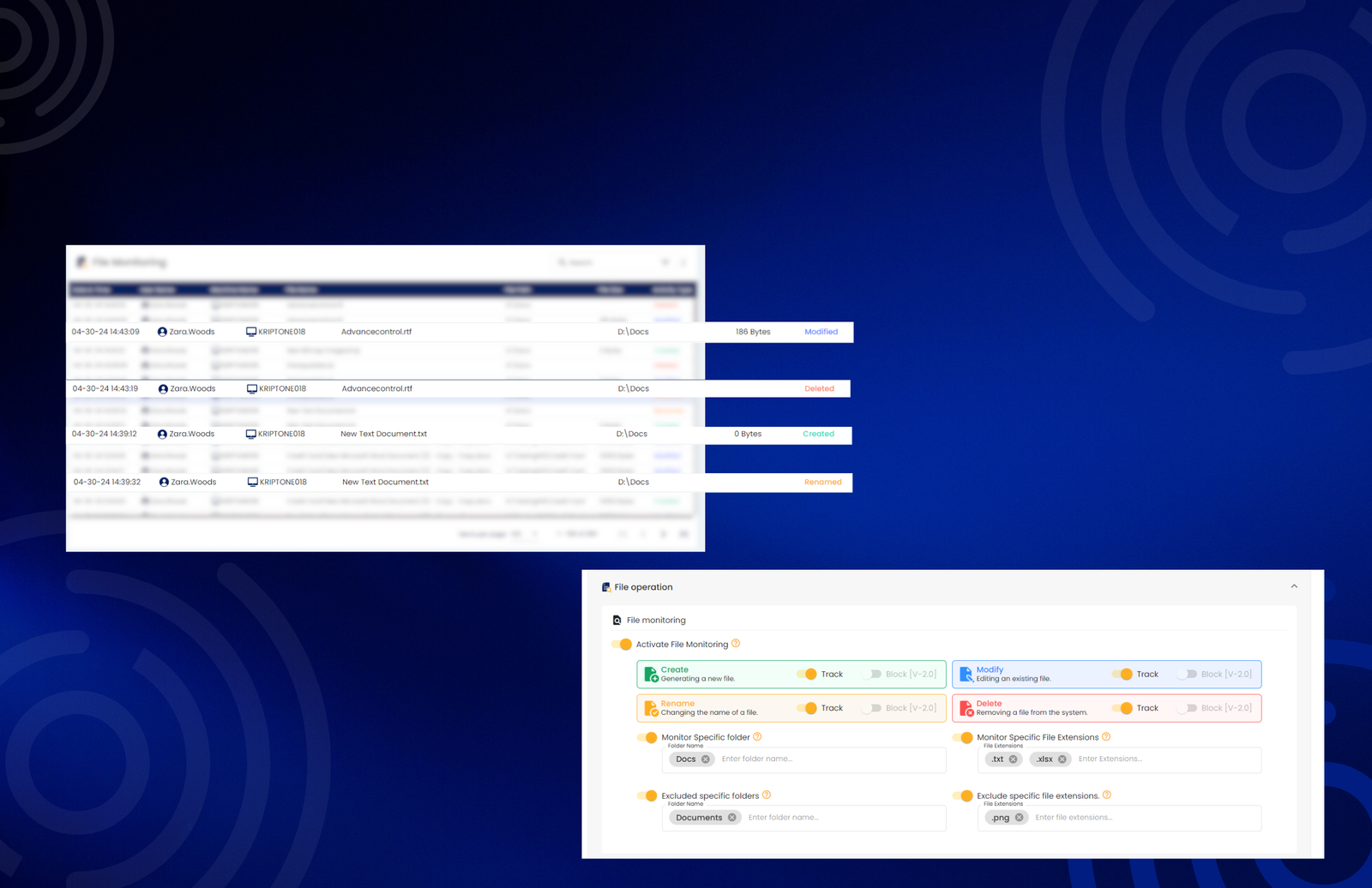
Monitor file access and modifications to prevent data breaches. Detect unauthorized access and ensure compliance with data protection regulations.
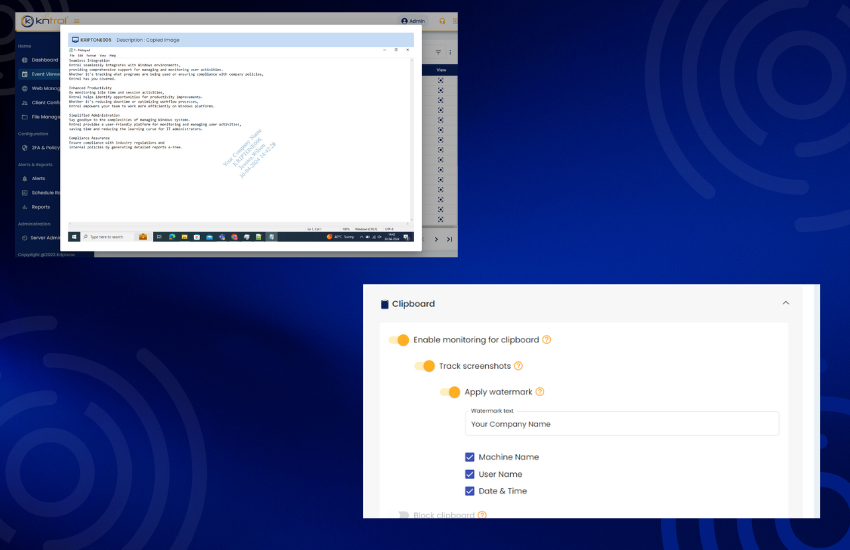
Protect sensitive information with automatic watermarking. Add unique identifiers to screen captures and prevent unauthorized distribution.
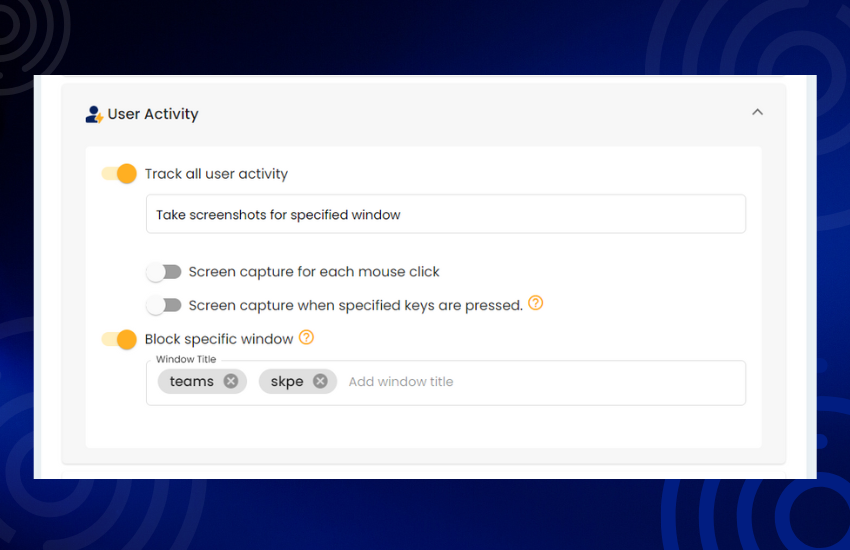
Control screen capture functionality to protect intellectual property. Prevent unauthorized capture of sensitive information.
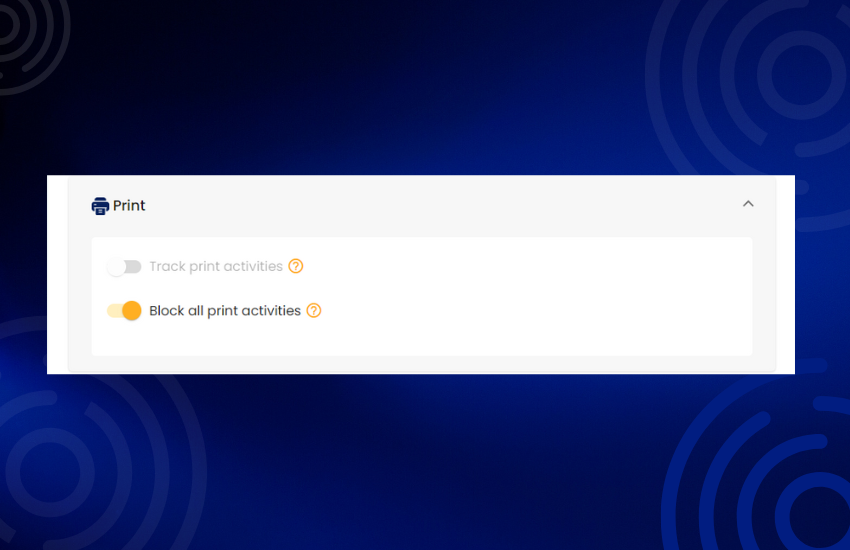
Manage printer usage and prevent unauthorized printing. Enforce print policies and reduce printing costs.
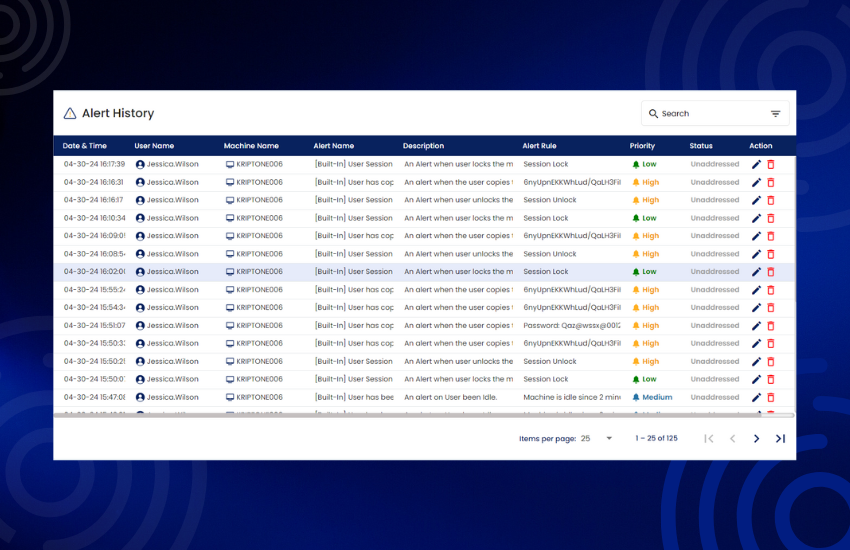
Receive real-time alerts for security incidents and policy violations. Stay informed and take immediate action to mitigate risks.
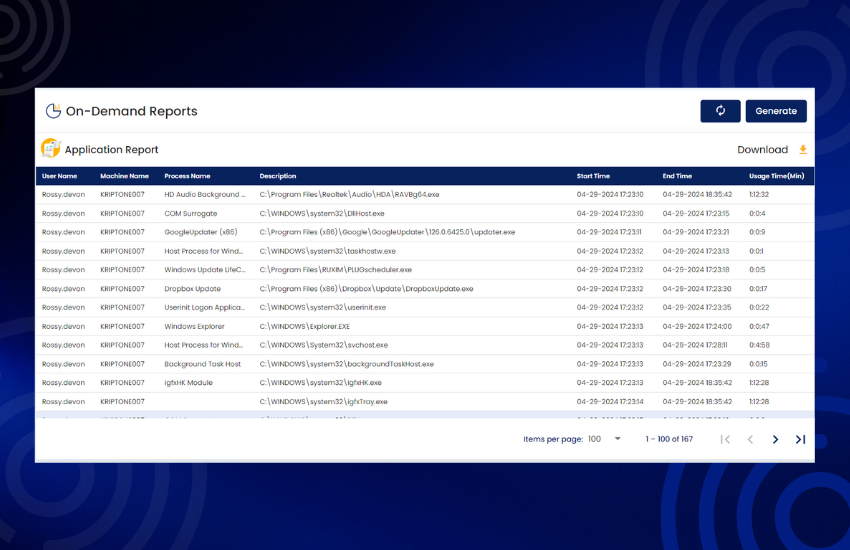
Generate detailed reports on user activities, security incidents, and compliance status. Gain actionable insights and demonstrate compliance with ease.

To track and manage file operations like creation, modification, renaming, and deletion..
To track and manage file operations like creation, modification, renaming, and deletion..

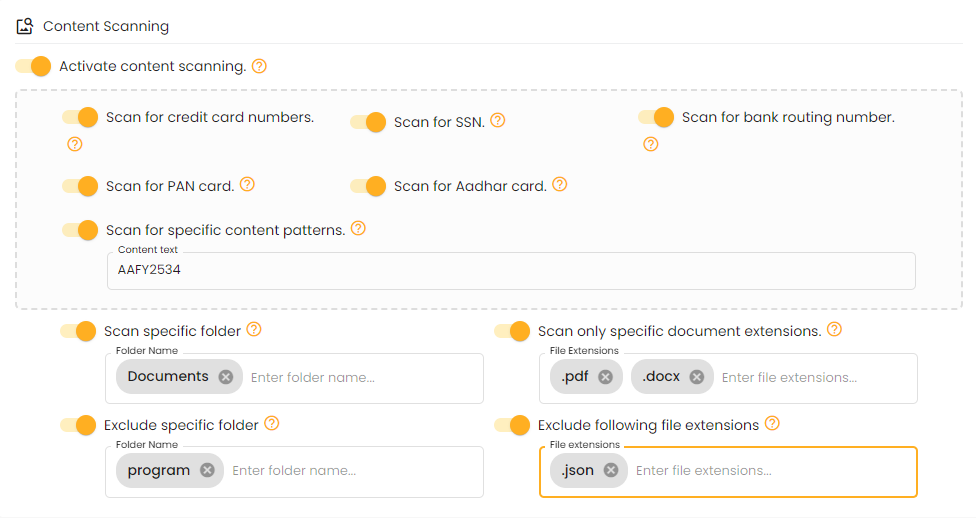
To monitor and analyze the content of files to ensure security and compliance.
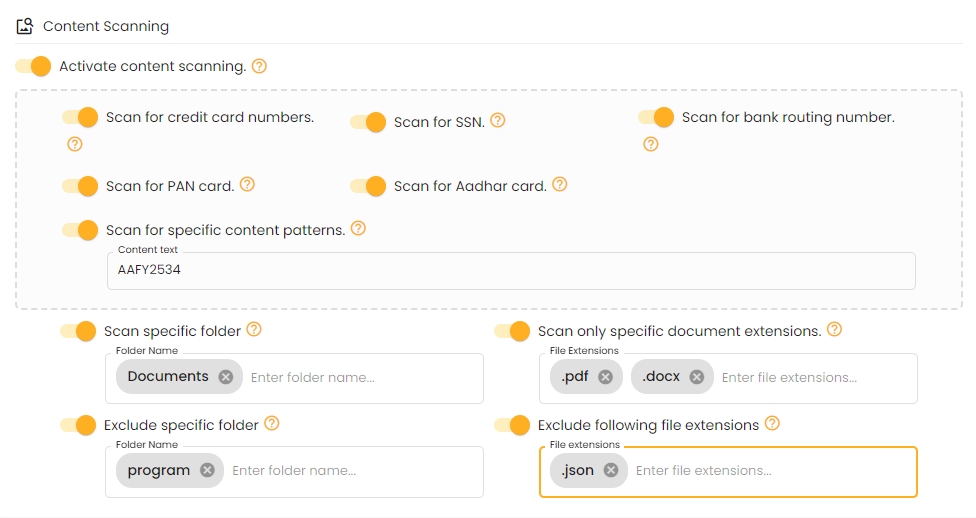
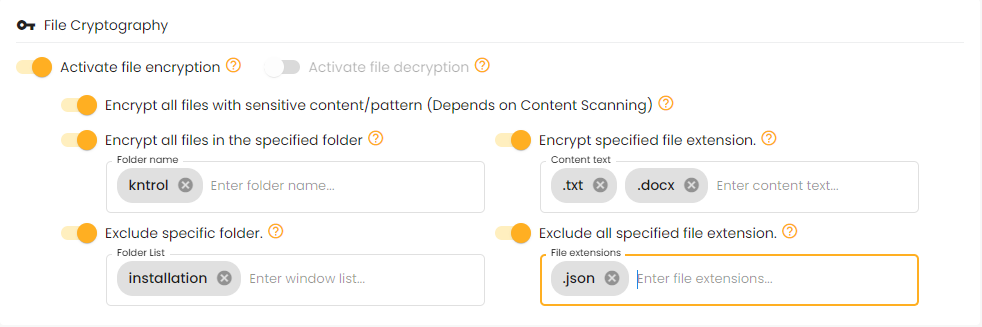
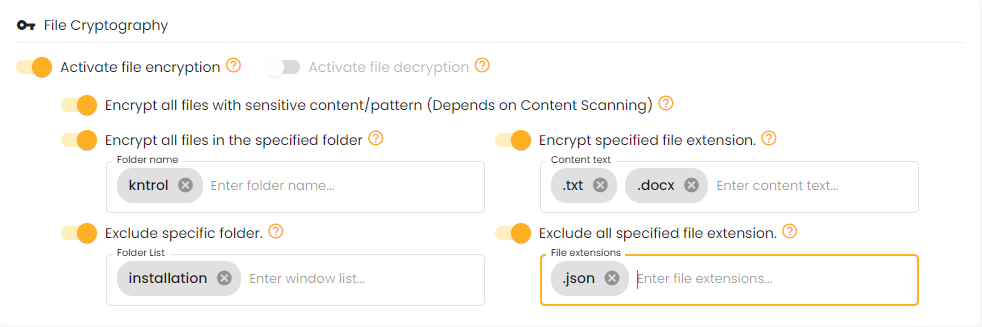
File encryption converts files into an unreadable format using cryptographic algorithms, ensuring only authorized users with the decryption key can access them. This safeguards sensitive information from unauthorized access, data breaches, and cyberattacks.
File encryption converts files into an unreadable format using cryptographic algorithms, ensuring only authorized users with the decryption key can access them. This safeguards sensitive information from unauthorized access, data breaches, and cyberattacks.

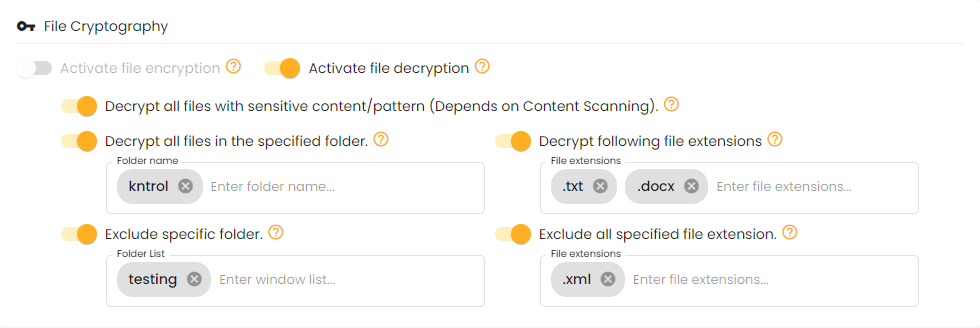
File decryption converts encrypted files back into their readable format using cryptographic algorithms and a decryption key. This allows authorized users to access the original data, ensuring that only those with permission can view sensitive information, maintaining security and data integrity.
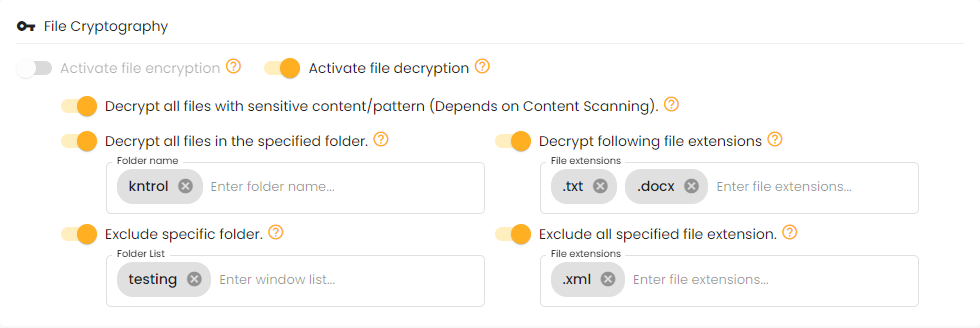
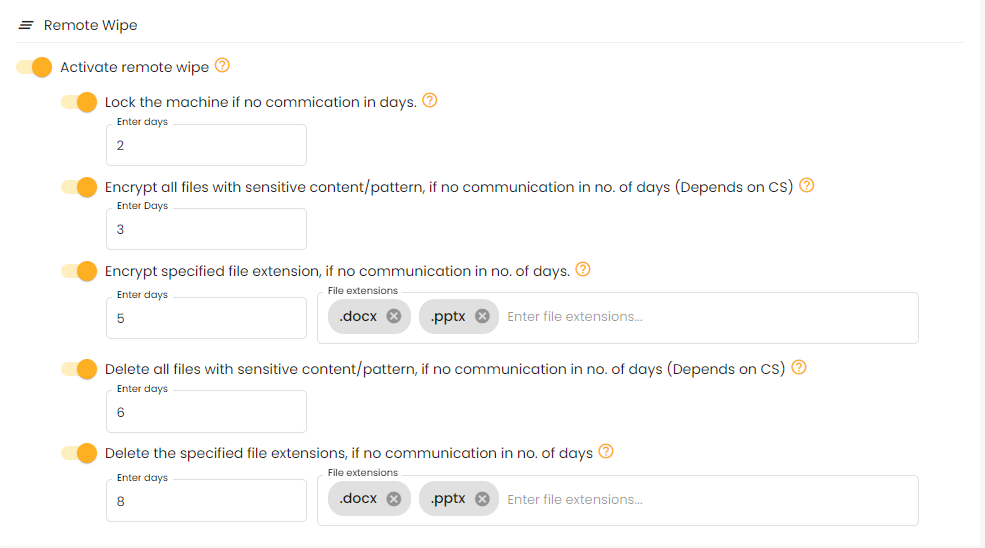
To protect data on a device that has lost communication, ensuring data security through locking, encrypting, or deleting files.
To protect data on a device that has lost communication, ensuring data security through locking, encrypting, or deleting files.

Contact our team to find out how Kntrol can help with data security and compliance.