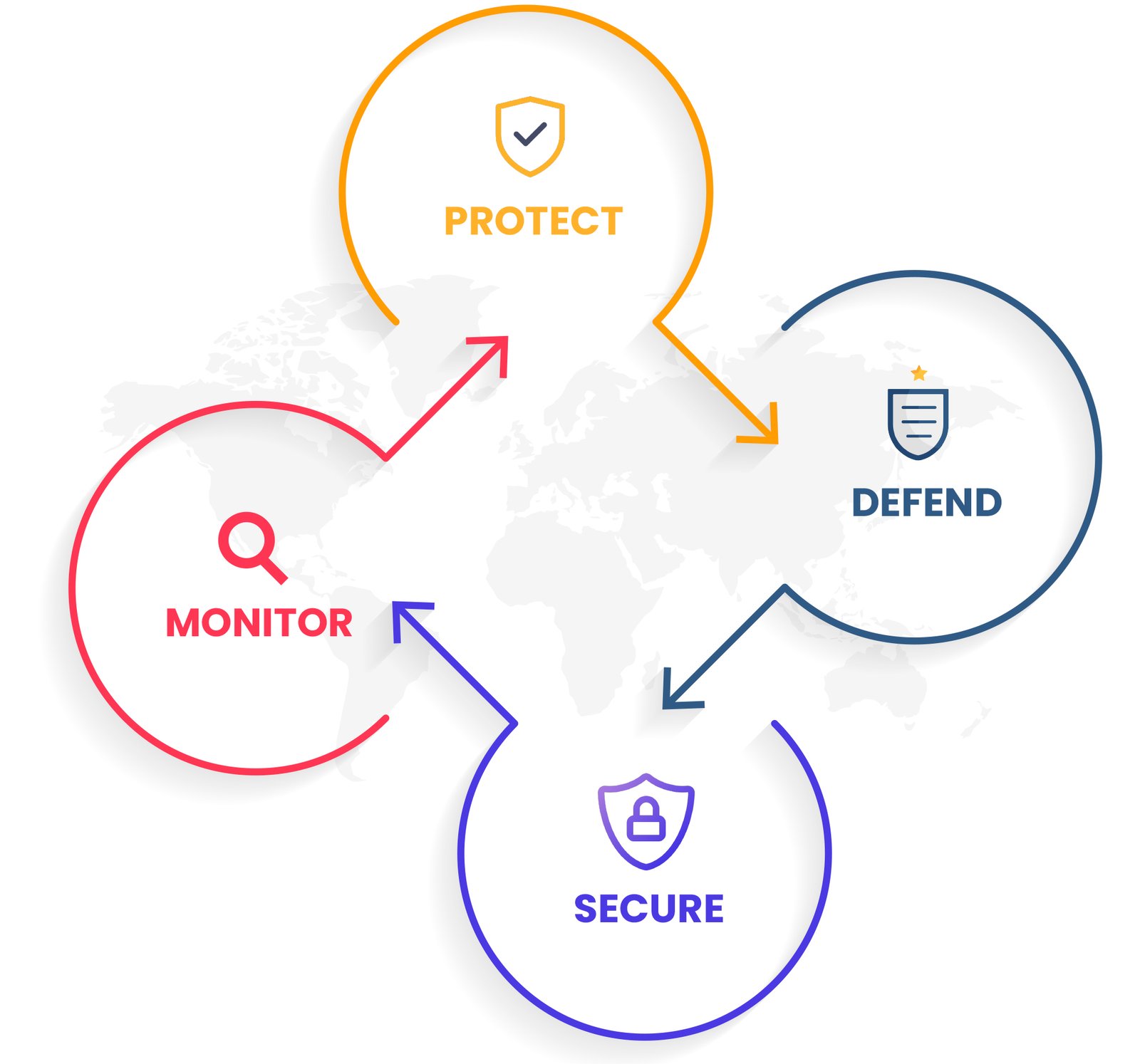
Why Choose Us
Kntrol - Proactive Security and Compliance
Behavior Pattern Tracking
Kntrol goes beyond simple monitoring by actively tracking and analysing behaviour patterns. By doing so, it identifies anomalies and potential threats before they escalate.
Enhanced Organizational Visibility
Kntrol provides comprehensive visibility across the organization's endpoints. This allows administrators to have a clear understanding of the security posture and potential risks, enabling proactive threat mitigation.
Policy Compliance
Kntrol ensures compliance with defined security policies and regulatory requirements. Through its robust features, it enforces adherence to established protocols, reducing the risk of breaches and ensuring regulatory compliance.