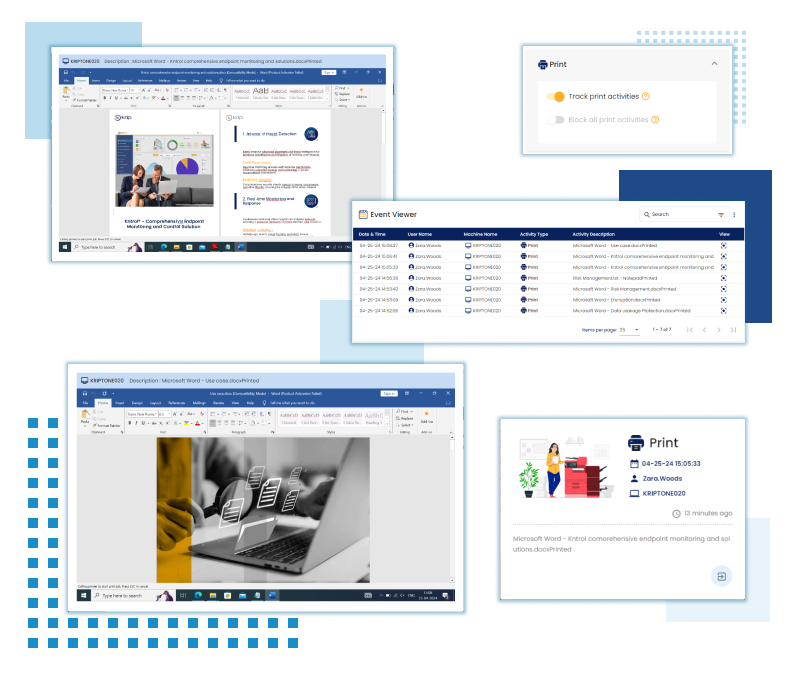
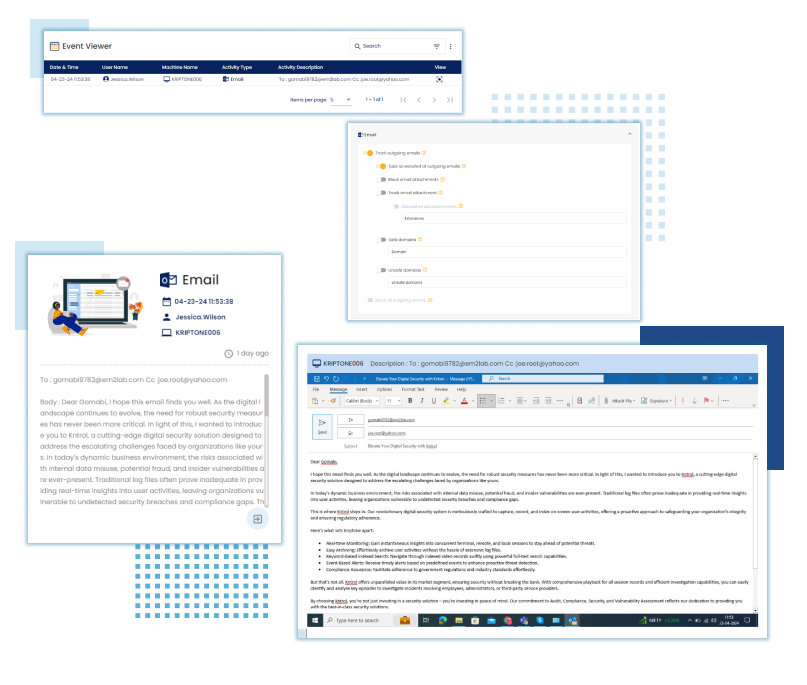
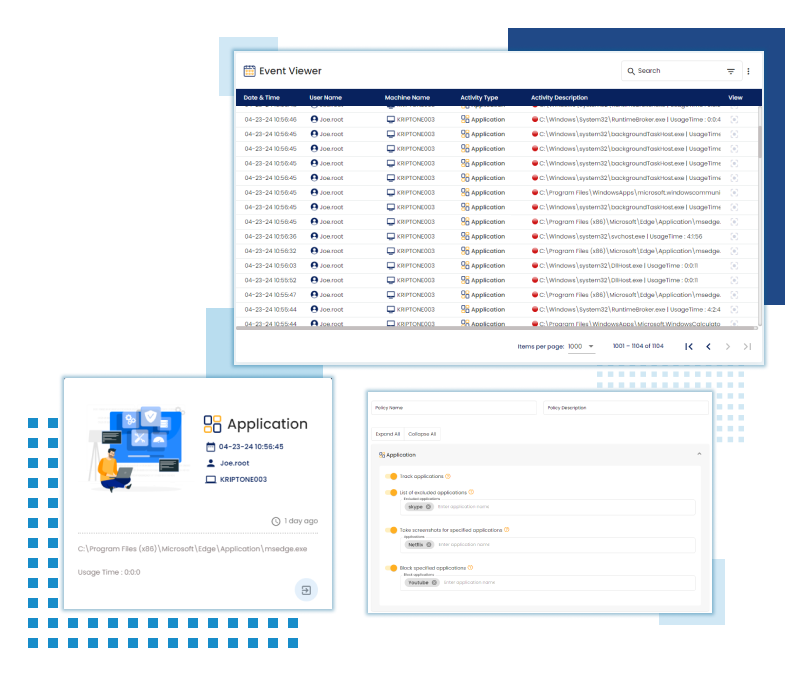
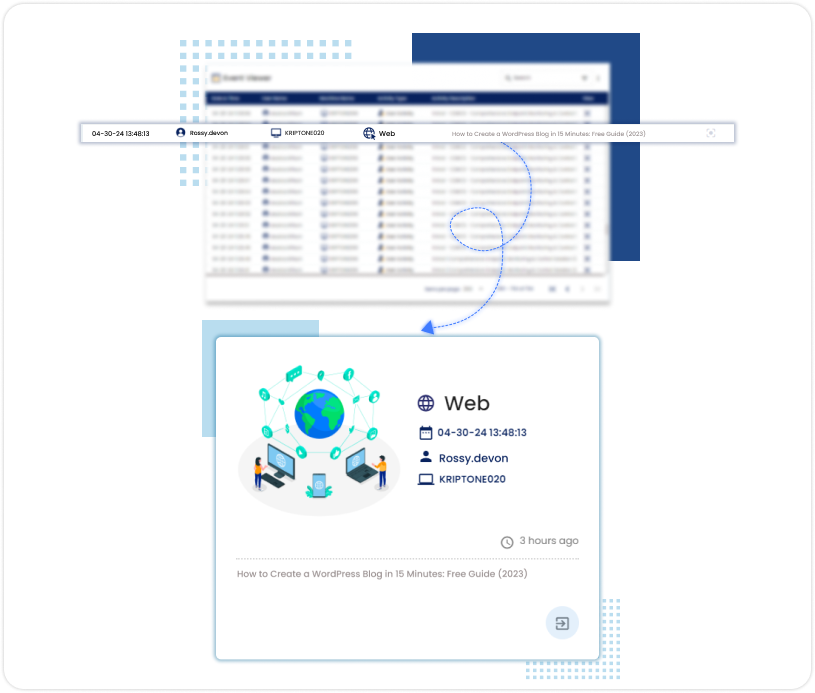
FILE MONITORING
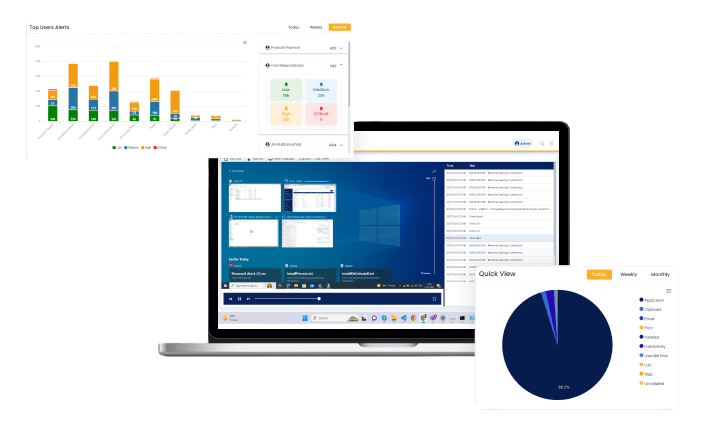
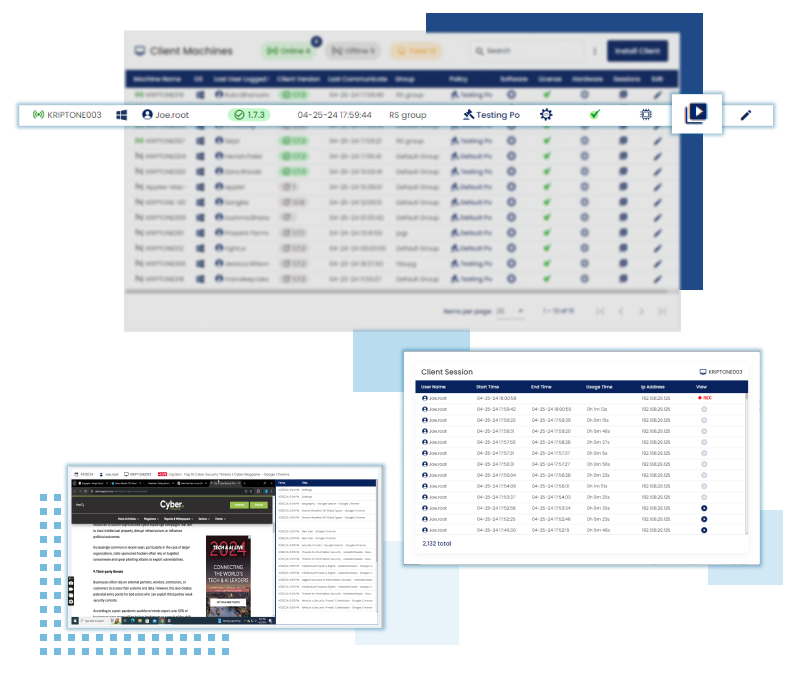
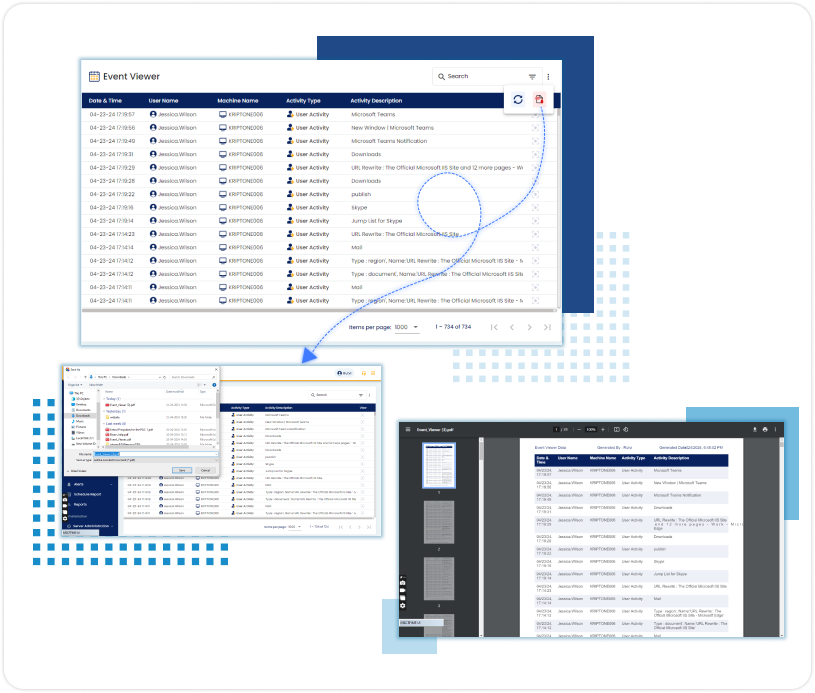
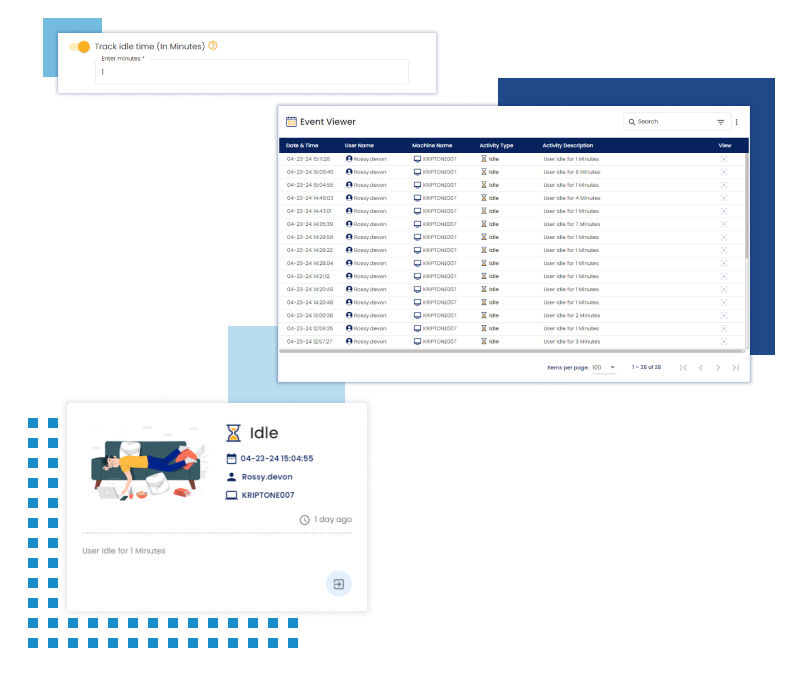
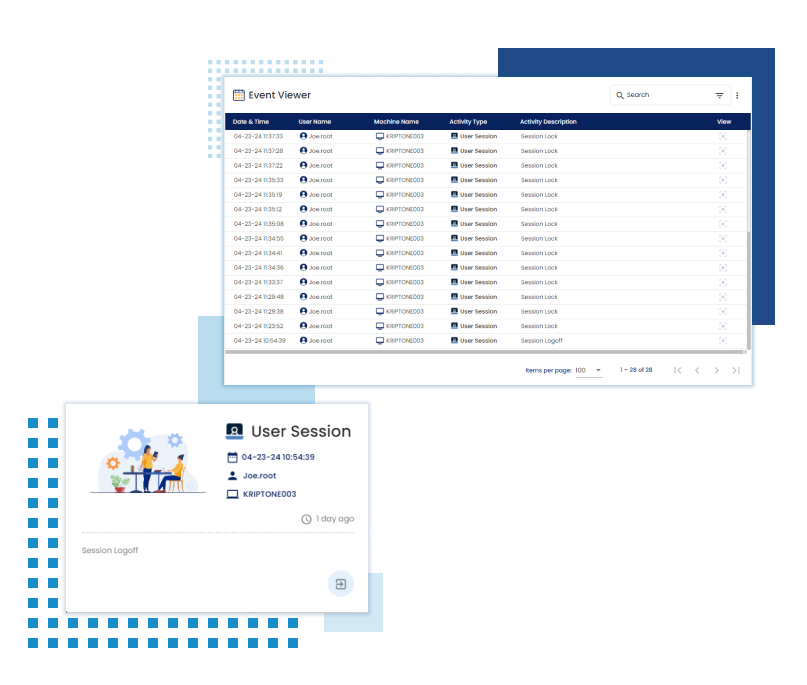
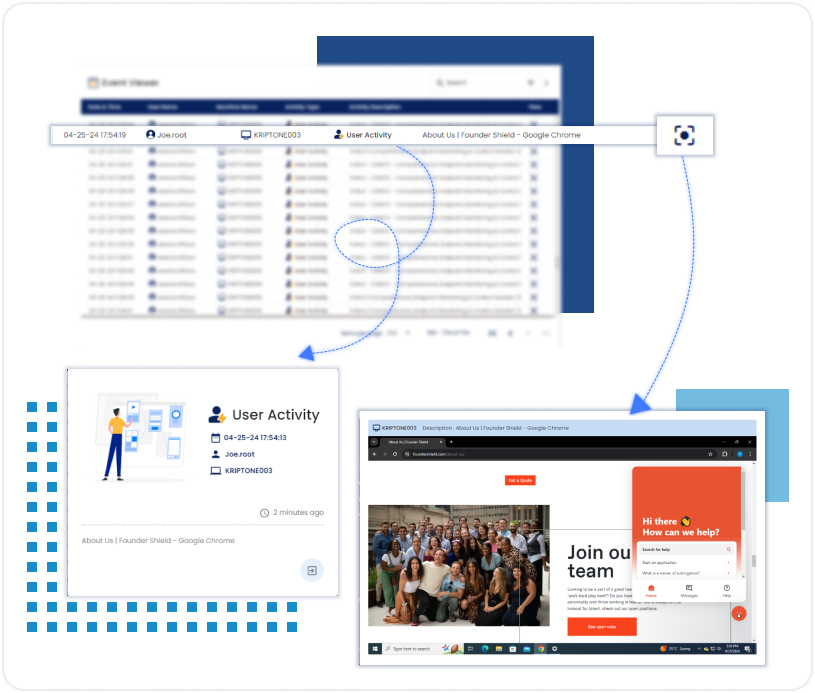
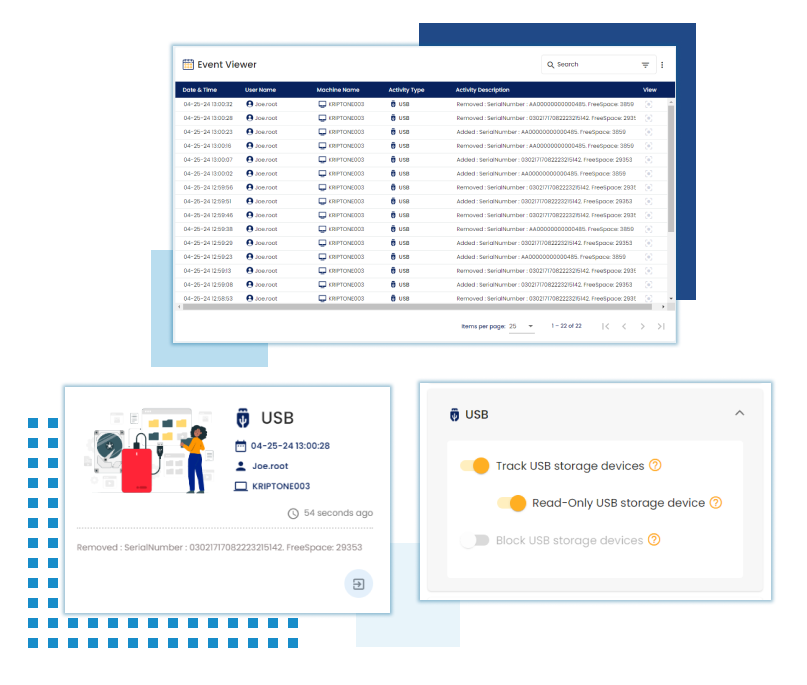
The file monitoring feature tracks and manages file activities like creation, modification, renaming, and deletion to maintain security and data integrity. Users can configure it to focus on specific folders and file types while excluding others, optimizing monitoring efficiency.